Centralised Control of Sensitive Assets
WALLIX Bastion is dedicated to protecting your infrastructure against cyber risks

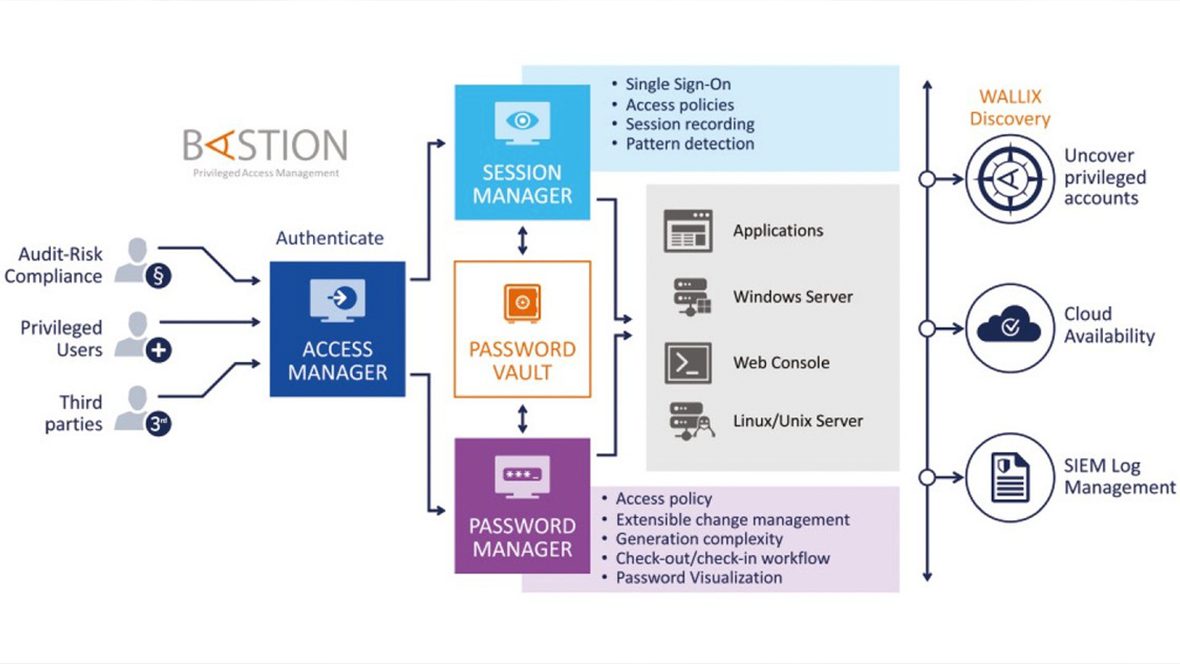
Gain real-time visibility and analysis of all privileged activities, including full session recording and metadata extraction. With WALLIX Bastion, you can limit visibility of resources from users between primary and target accounts. Ensure that only the authorised users can access the certain resources at specified times with advanced access workflows. Identify suspicious behaviour and trigger automatic session termination. All allowing you to protect credentials, even when leaked, with automatic rotation, periodically or based on check-in/check-out.
The WALLIX Bastion solution supports all technical environments with dedicated protection for on-premise, multisite deployments, and public/private clouds. It’s also compatible with all the leading cloud platforms and can be found on leading Cloud marketplaces.
Why Privileged Account Management? (PAM) Is it really needed?
Across all sectors, a top security priority is guaranteeing control and traceability over third-party service providers in addition to meeting the criteria of a range of mandatory compliance regulations (GDPR, NISD, LPM, PCI-DSS, etc.). PAM (Privileged Access Management) addresses these requirements while strengthening the security of remote connections and protecting the organisations’ strategic resources. Watch the video below to discover 5 real-life scenarios where you need Privileged Access Management:
5 Real-Life Privileged Account Management Scenarios
Wallix Bastion Account Manager Authorisation Management
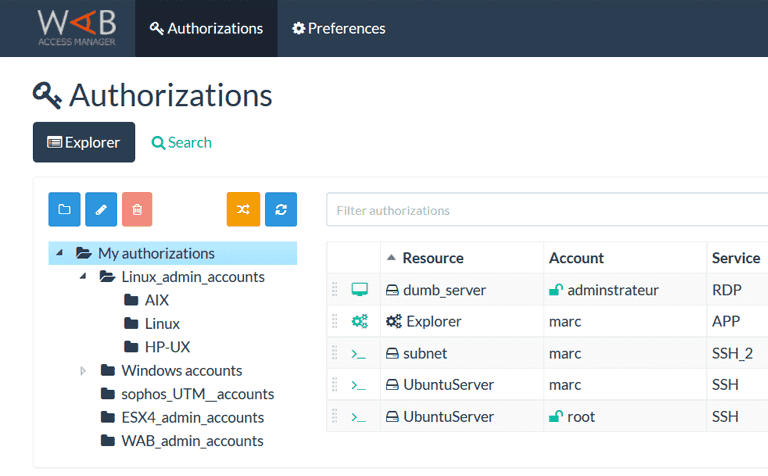
Control Access to Resources
Real-time visibility of privileged activities including session recording and metadata extraction
- Authorised users can access authorised resources
- Credential protection with automatic rotation
- Limited resource visibility and account segregation
- Identify suspicious behaviours
Deploy your Defence
- Centralise user management and target systems
- Create and enforce password policies for internal and external users
- Set up authorisation rules and conditions to automatically grant or deny system access
Simplified Build & Run
Solution requiring minimal time to administer, resulting in optimised Total Cost of Ownership
- Deploy quickly without interruption to workflows
- Easy to use and easy to integrate, Bastion minimises the ‘Build & Run’ intervention time for IT
- Integrate seamlessly with existing security (e.g. AD)
Monitor and Review
- Choose to receive automated alerts for when privileged sessions begin
- Monitor sessions in real-time with WALLIX 4-Eyes
- Audit sessions via full recording and metadata extraction
Ensure Regulatory Compliance
Benefit from an all-in-one solution to meet access and data regulations, and compliance requirements
Ensure internal security meets industry standards by protecting and tracing critical data access
Comply with specific regulation requirements with access control, monitoring, and audit capabilities
Terminate Malicious Attempts
- Distinguish legitimate user sessions from suspicious activity such as unusual command lines or forbidden applications
- Raise alarms or terminate sessions when malicious activity is detected
An introduction to WALLIX Bastion
Set up Privileged Access Management in less than 15 minutes!
Arrange a FREE online demo or trial with us see how it works live in your working environment.
For more information on WALLIX Bastion Privileged Account Management (PAM) please contact us.
Get in touch