Thycotic Privilege Manager: Implement Least Privilege Through Application Control

Thycotic’s Privilege Manager provides advanced security to manage application rights with a combination of privilege management, application whitelisting, and real-time application reputation and threat intelligence for both Windows and Mac endpoints.
Privilege Manager uses proactive endpoint protection against ransomware and evolving advanced threats, whilst allowing you to enforce least privilege policy without impacting productivity, through a easy to manage application control solution. Save time and reduce help desk calls.
SIMPLE LEAST PRIVILEGE IMPLEMENTATION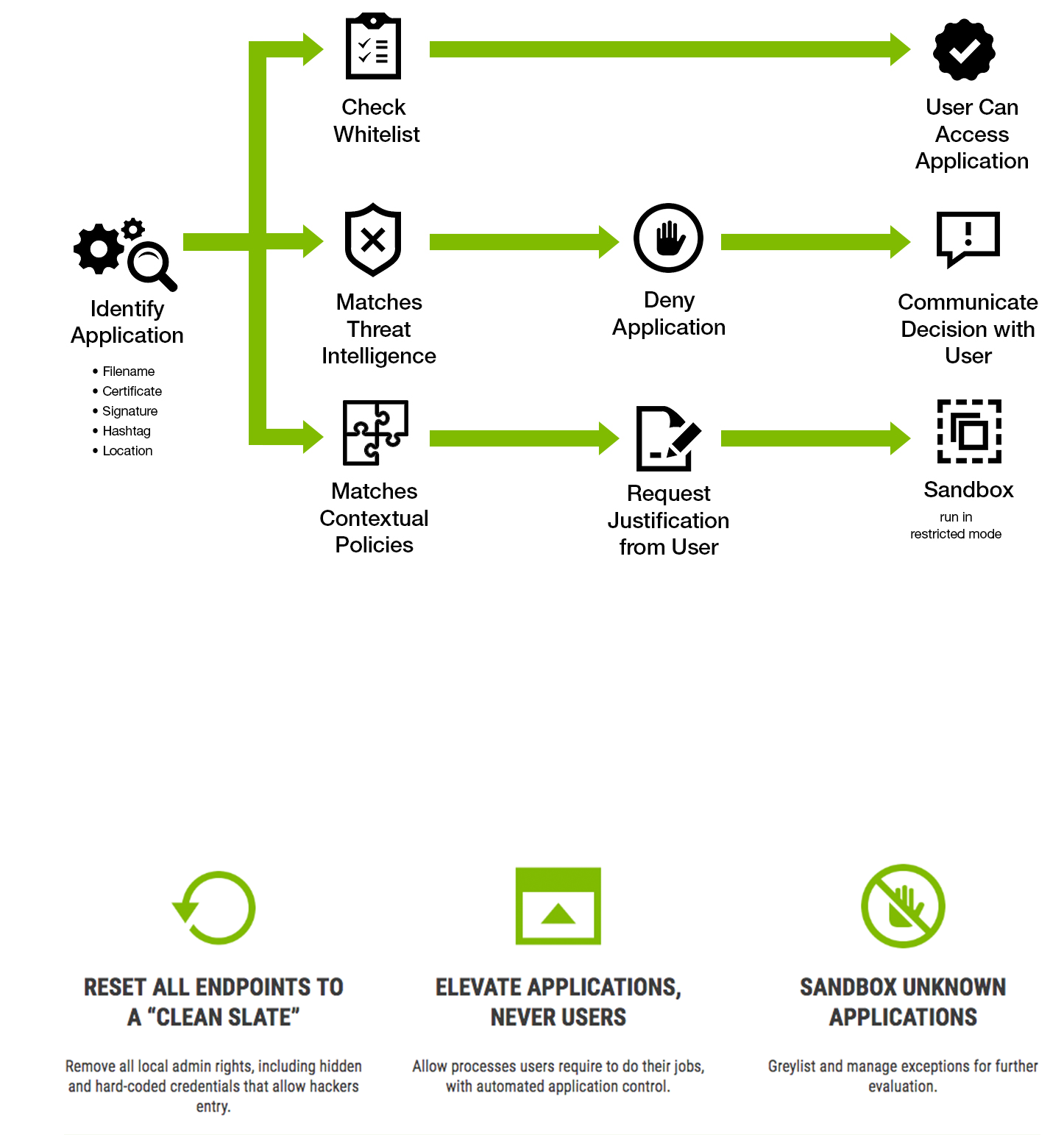
Remove All Admin Credentials from Endpoints at Once.
Local admin accounts are privileged accounts. If a local admin clicks on a malicious link and downloads malware, their workstation could become “patient zero” in a catastrophic attack. When hackers gain privileges on one machine they can progress through your network and even cover their tracks by changing event logs.
Privilege Manager automatically removes admin rights from domain and non-domain managed endpoints, including hidden or hard-coded credentials. As a result, virtually all critical vulnerabilities are mitigated. By focusing your endpoint protection plan first on removing privileged credentials you’ll tighten your attack surface and avoid spending time and resources on reactive detection and remediation.
PRODUCTIVITY THROUGH APPLICATION CONTROL
Easy for IT/Desktop Support. Seamless for Users.
Most least privilege policies fail because removing admin rights negatively impacts users and creates more work for IT support teams.
Privilege Manager uses policy-based controls to elevate applications users need, without requiring admin credentials or requesting IT support. It automatically adds trusted applications to a whitelist, relies on the latest intelligence from threat databases such as VirusTotal to create blacklists, and adds unknown applications to greylists. Sandboxing elevates applications in a limited way so they don’t have access to system controls or OS configurations. Because Privilege Manager elevates applications and not the user, it never leaves a window open for hackers.
SET POLICIES BASED ON SECURITY AND BUSINESS REQUIREMENTS
IT Security teams have granular, contextual control:
- On who may run processes that require administrative credentials.
- If processes can run on certain endpoints but not others.
- If processes are allowed in certain regions or during certain times of day.
- Whether to allow child processes to run.
Business Productivity
- Business users can still run conferencing applications such as GoToMeeting and WebEx.
- Remote workers can continue to install printer drivers.
- Power users or developers can continue to run applications that connect to SQL Studio and DevOps tools and run scripts that connect to code libraries, and cloud controls.
For pricing and more information on Thycotic Privilege Manager please contact us.
GET IN TOUCH












































