Powerful protection for business endpoints
Industry leading, multi-layered, cloud-managed security
Malwarebytes Endpoint Protection provides complete malware protection and remediation with precise threat detection, proactive threat blocking, and thorough remediation, driven from the cloud and easy to use for organisations of all sizes. Malwarebytes employs innovative machine learning & artificial intelligence, and offers a centralised cloud-based management console where businesses get continuous visibility into endpoints.
FREE analysis report on your antivirus
Request a threat reportFREE Trial with specialist support
Request a free trialFREE security consultation with an engineer
Consult with an expertUnlike other antivirus solutions, EPP is comprehensive protection built for speed. Take a look at the product features tab to see a complete list of features.
Simplified Management
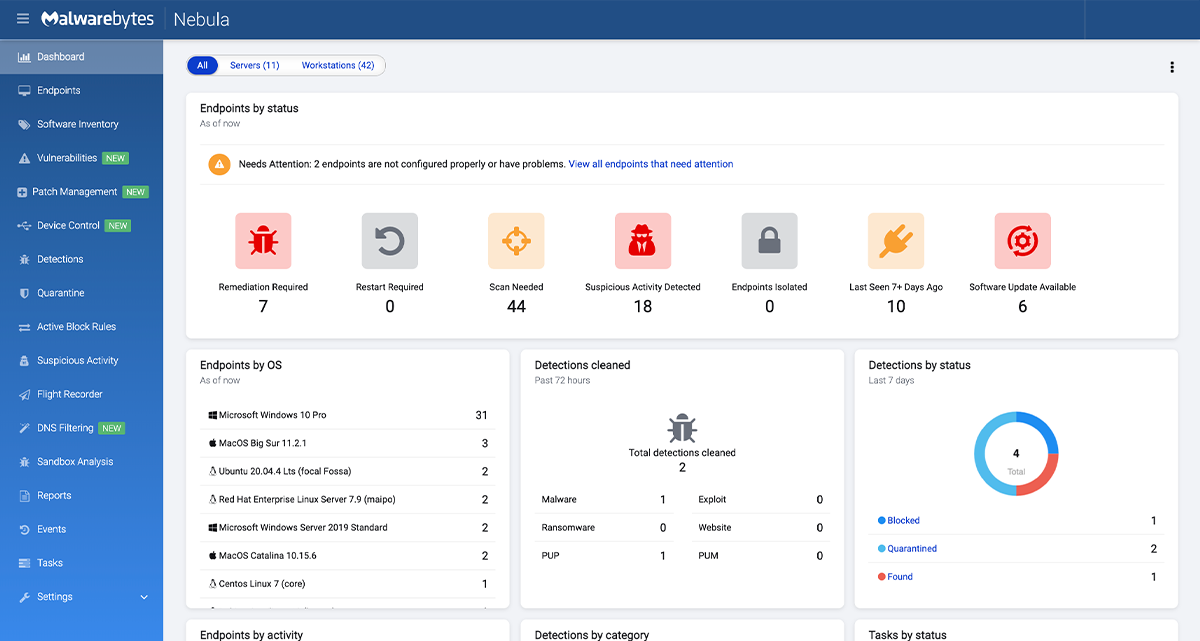
Avoid the complexity of multiple consoles managing a patchwork of one-off tools. Malwarebytes gives you a single dashboard with an easy-to-use interface, delivering real-time status of events and device health across your network. The user interface also controls all functionality across the full suite of endpoint protection software. This includes the ability to easily prioritise remediation via multiple filters, like severity of threat, physical location, and other criteria.


Lightweight Agent
Unlike old-school signature-based approaches that wait until attacks kick in, Malwarebytes Endpoint Protection finds and blocks threats before devices are infected. This happens by recognising and preventing both hostile code and bad behaviour by people. Blocking threats your previous solution missed, including web-based attacks, zero-day malware, ransomware, PUPs, PUMs, infections from USB peripherals, all via a single agent.
Malwarebytes Endpoint Protection Overview
Malwarebytes Cloud Management Dashboard
For more information on the Malwarebytes Endpoint Protection, please contact us.
Get in touch
























 Knowledgebase Articles
Knowledgebase Articles



















