Industry-best threat removal and remediation
Real-time cloud-based protection from malware, ransomware, zero-day exploits, phishing and more
Malwarebytes Endpoint Detection and Response for Windows and Mac offers enterprise-class endpoint protection, advanced threat hunting, and reliable isolation, remediation, and response to cybersecurity attacks. Offering a centralised cloud-based management console, businesses get continuous visibility into endpoints with Malwarebytes EDR as it protects against ransomware, malware, trojans, rootkits, backdoors, viruses, brute force attacks, and “zero-day” unknown threats.
FREE analysis report on your antivirus
Request a threat reportFREE trial with specialist support
Request a free trialFREE security consultation with an engineer
Consult with an expertUnlike other EDR solutions, this solution doesn’t just alert, it fixes. Take a look at the product features tab to see a complete list of the protection and response features.
Easy, effective, and efficient
Malwarebytes Endpoint Detection and Response for Windows and Mac can easily replace or augment other endpoint security solutions, including Microsoft Defender. Using unique Anomaly Detection machine learning, it not only detect known threats, but finds unknown “zero-day” threats. EDR offers remote worker optimisation, industry-leading efficiency, high return on investment (ROI), and low total cost of ownership (TCO).


Isolate, remediate, and rollback
If an endpoint is attacked, you can easily halt malware from spreading and causing harm by isolating it from the rest of the network. Next, find and reverse all major and subtle changes that were made by malware. EDR uses local cache on each endpoint, storing all relevant changes to the device for up to 72 hours. If you’re infected, Malwarebytes simply backs out device changes and restores files that were encrypted, deleted, or modified.
Why Malwarebytes Endpoint Detection & Response?
Malwarebytes Cloud Management Dashboard
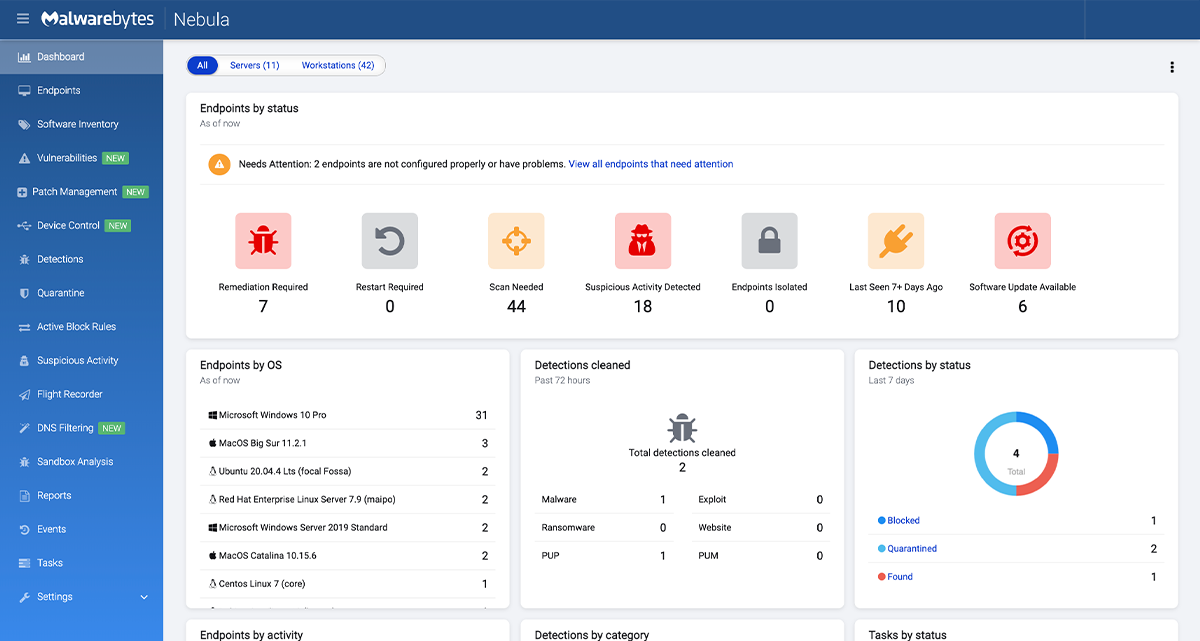
For more information on the Malwarebytes Endpoint Detection & Response, please contact us.
Get in touch
























 Knowledgebase Articles
Knowledgebase Articles



















