Thycotic Secret Server On-Premise: Privileged Account Management Software
 AN ENTERPRISE-CLASS PASSWORD MANAGEMENT VAULT
AN ENTERPRISE-CLASS PASSWORD MANAGEMENT VAULT
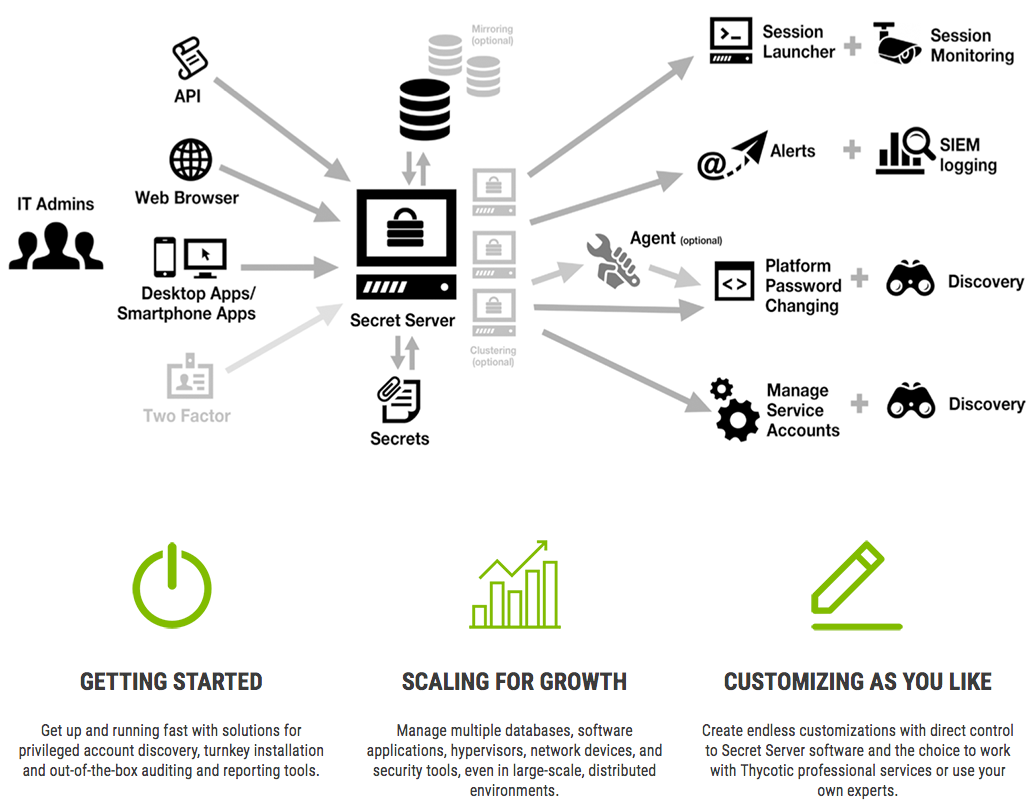
With Secret Server enterprise password management software, you and your colleagues can control access to critical passwords in one centralised, web-based repository. The password management software offers permissioned users secure access to passwords and other privileged information.
Lock down sensitive account passwords on-premises. Integrate with Active Directory.
- Get full audit reports for compliance mandates.
- Automate privileged account discovery and password changing.
- Windows local admin accounts, service/application accounts, UNIX/ Linux, web and more.
ELIMINATE INTERNAL AND EXTERNAL THREATS
Don’t just vault IT credentials. Know exactly who has access to key systems.
- Real-time session monitoring, recording and keylogging keeps a watchful eye on IT.
- Integrate with SIEM and vulnerability scanners for heightened network security.
MANAGE SERVICE ACCOUNTS
- Never lose track of service accounts or application pools again.
- Instantly discover service accounts on the entire network.
- Rotate service account passwords without breaking dependencies.

Choose the edition that is right for you. Secret Server seamlessly scales to meet your organisation’s evolving IT challenges. Gain security and reduce risk through multiple levels of auditing, monitoring, and alerts.
Streamline IT operations with automatic password changing and account discovery. Ongoing feature development ensures the software is always up to the demands of world-class enterprises.
Request a Web Demo Request a Free Trial
For more information and general guidance on Thycotic products please contact us.





























 Knowledgebase Articles
Knowledgebase Articles

















